Entity authentication is the procedure of mutual authentication of UE or USIM and the network. There are few fundamental requirements for this procedure:
- First to permit the network to check whether the identity provided by the mobile station is acceptable or not;
- Second to provide parameters enabling the mobile station to calculate a new UMTS ciphering key;
- Third to provide parameters enabling the mobile station to calculate a new UMTS integrity key;
- Fourth to permit the mobile station to authenticate the network.
Authentication Vectors
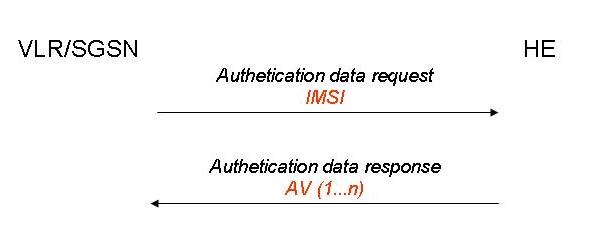
The Authentication Vectors are used in Entity Authentication and Security procedures.
The VLR/SGSN starts this procedure by requesting authentication vector to the HE/AuC.
When HE/AuC receives the request from the VLR/SGSN it retrieves the calculated authentication vectors AV (1…n) from the HLR database and sends it to the VLR/SGSN in Authentication data response.
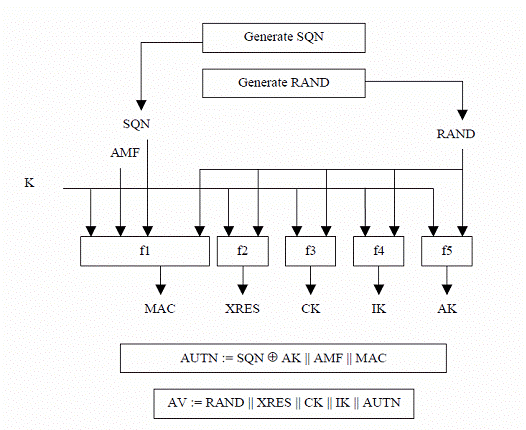
The Authentication Vectors generation procedure in HE/AuC is as follows:
HE/AuC first generates a fresh sequence number SQN and an unpredictable challenge RAND.
After that the following will be calculated:
Message Authentication Code MAC = f1K (SQN || RAND || AMF), f1 is the message authentication function.
Expected response XRES = f2K (RAND)
Cipher key CK = f3K (RAND), f3 is a key generating function
Integrity key IK = f4K (RAND), f4 is a key generating function.
Anonymity key AK = f5K (RAND)
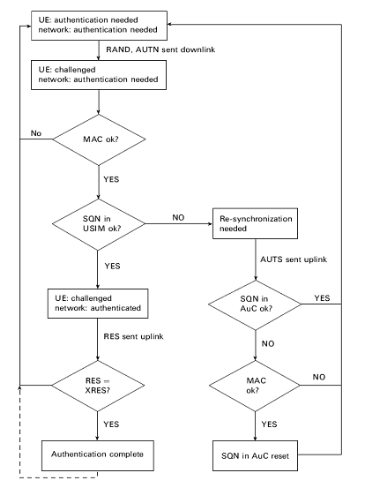
Authentication Procedure
The authentication procedure is as follows:
The steps are as follows:
Step#1
In the beginning both the USIM and the Network are not authenticated. That means USIM does not know whether the network is a real network and network does not know whether the USIM is a valid Subscriber.
Step#2
Network starts the authentication procedure by sending the User Authentication Request with the parameter RAND and AUTN.
Step#3
After UE receives RAND and AUTN, the USIM first computes the anonymity key AK = f5K (RAND) and retrieves the SQN = (SQN ![]() AK)
AK) ![]() AK
AK
After that UE computes XMAC = f1K (SQN || RAND || AMF) and compares with MAC.
If both are different UE send user authentication reject back to the VLR/SGSN.
If the USIM finds the SQN is not in the correct range, it sends synchronization failure.
Step#4
UE sends expected response RES to the VLR/SGSN.
If RES = XRES, then the authentication procedure completes
Message sequence from UE point of view
[UE <– NW] DOWNLINK DIRECT TRANSFER (IDENTITY REQUEST)
[UE –> NW] UPLINK DIRECT TRANSFER (IDENTITY RESPONSE)
[UE <– NW] DOWNLINK DIRECT TRANSFER (AUTHENTICATION REQUEST)
[UE –> NW] UPLINK DIRECT TRANSFER (AUTHENTICATION RESPONSE)
[UE <– NW] SECURITY MODE COMMAND
[UE –> NW] SECURITY MODE COMPLETE
References
3G Security: Security architecture: 3GPP TS 33.102